SonicWall - How to Globally Block Facebook Pokes Using the Application Firewall
Introduction
At times, administrators may want to block specific functions in Facebook, like poke, from being used by the whole company.
Prerequisites
- SonicOS 5.8.0.2 or greater
- Licensing for Application Firewall
- Licensing for DPI-SSL
- One of the following SonicWALL Security Appliance Platforms:
- TZ 215
- NSA 220
- NSA 240
- NSA 250M
- NSA 2400
- NSA 3500
- NSA 3600
- NSA 4500
- NSA 4600
- NSA E5500
- NSA 5600
- NSA E6500
- NSA 6600
- NSA E7500
- NSA E8500
- NSA E8510
Components Used
The information in this document is based on the SonicOS 5.8.1.
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, make sure that you understand the potential impact of any command.
Configure the Firewall
In this section, you are presented with the information to configure the Firewall to block pokes in Facebook from being used by the whole company.
The first two steps are to enable Application Rules on a global level and on a local zone level. Enabling Application Rules globally turns it on for the whole firewall, but Application Rules will not work for a user until it is turned on locally on the network zone that the user’s computer is connected to.
The next step is to enable DPI-SSL. This enables the firewall to do Deep Packet Inspection of Secure Socket Layer traffic. SonicWall does this by becoming a “Man-in-the-middle” by capturing the incoming SSL traffic, decrypting that traffic, scanning that traffic, re-encrypting the traffic with its own certificate, and then sending the traffic downstream. Facebook and Facebook poke run over SSL and therefore require DPI-SSL in order to scan and block that traffic.
Application Rules can be applied to users, groups, or globally. In this example, we chose to apply this policy only to an individual named Al Dente. SonicWall can look up users and groups in both the local user database and Microsoft Active Directory. Al Dente is a user that exists in Windows Active Directory.
SonicWall groups all of its Application Signatures into groups of Applications. Applications are then grouped into Categories.
Facebook Poke App Signatures are grouped into the “SOCIAL-NETWORKING Facebook” Application group. The “SOCIAL-NETWORKING Facebook” Application group is included in the “SOCIAL-NETWORKING” Category.
There are 2 Facebook Poke Application signatures that apply to the SOCIAL-NETWORKING Facebook Application. You must add both signatures to this Match Object so that the firewall knows what to look for.
Facebook Poke has 2 Application signatures:
- SOCIAL-NETWORKING Facebook – Poke Action 1 (6668)
- SOCIAL-NETWORKING Facebook – Poke Action 2 (6669)
For other Application Signatures that are on the SonicWall firewall, you can look up which Category group and Application group an Application Signature is in by using the search engine on the following page: https://software.sonicwall.com/applications/app/index.asp?ev=cat
Configuration Stages
There are five stages to this configuration process:
- Stage I – Enable App Rules Global Setting on the Firewall
- Stage II – Enable App Rules Local Setting on the LAN Zone
- Stage III – Enable DPI-SSL for the Application Firewall
- Stage IV – Create Match Object
- Stage V – Create App Rule
Other items included in this article:
- How to Test
- How to Troubleshoot
- Related Resources
- Stage I - Enable App Rules Global Setting on the Firewall
Complete these steps in the GUI in order to enable the App Rules Global setting on the firewall. Enabling Application Control globally turns it on for the whole firewall.
- Navigate to Firewall > App Rules.
- Check the box next to Enable App Rules to enable App Rules globally.
- Stage II - Enable App Rules Local Setting on the LAN Zone
After it is turned on globally, Application Rules will not work for a user until it is turned on locally on the network zone that the user’s computer is connected to. Complete these steps in the GUI in order to enable the App Control local setting on the LAN zone of the firewall.
- Navigate to Network > Zones.
- In the LAN zone, click on the Configure button.
- Check the box next to Enable App Control Service.
- Click the OK button.
- Confirm that App Control is enabled on the LAN zone by viewing the green check mark under the App Control column in the LAN row.
- Stage III - Enable DPI-SSL for the Application Firewall
The next step is to enable DPI-SSL. This enables the firewall to do Deep Packet Inspection of Secure Socket Layer traffic. SonicWall does this by becoming a “Man-in-the-middle” by capturing the incoming SSL traffic, decrypting that traffic, scanning that traffic, re-encrypting the traffic with its own certificate, and then sending the traffic downstream. Facebook and Facebook poke run over SSL and therefore require DPI-SSL in order to scan and block that traffic.
Complete these steps in the GUI in order to enable DPI-SSL for the Application Firewall.
- Navigate to DPI-SSL > Client SSL.
- Check the box next to Enable SSL Client Inspection then check the box next to Application Firewall.
- Click the Accept button to apply these changes to the firewall. This might require a reboot of the firewall.
- Stage IV - Create Match Object
Complete these steps in the GUI in order to create the Match Object. The Match Object is the application firewall signature that the application firewall is looking to match against.
- Navigate to Firewall > Match Objects.
- Click on the Add New Match Object button.
- On the Match Object Settings page, select the following:
- Object Name: Block Facebook Poke (type this in)
- Match Object Type: Application Signature List
- Application Category: SOCIAL-NETWORKING (76)
- Application: SOCIAL-NETWORKING Facebook (253)
Note: SonicWall groups all of its Application Signatures into groups of Applications. Applications are then grouped into Categories.
Facebook Poke App Signatures are grouped into the “SOCIAL-NETWORKING Facebook” Application group. The “SOCIAL-NETWORKING Facebook” Application group is included in the “SOCIAL-NETWORKING” Category.
For other Application Signatures that are on the SonicWall firewall, you can look up which Category group and Application group an Application Signature is in by using the search engine on the following page: https://software.sonicwall.com/applications/app/index.asp?ev=cat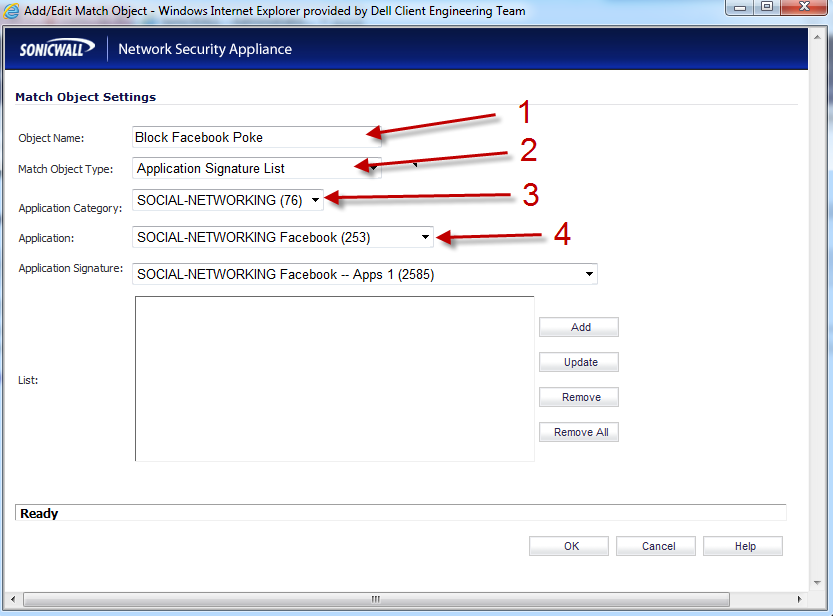
- There are 2 Application signatures that apply to the Facebook Poke Application. You must add both signatures to this Match Object so that the firewall knows what to look for.
Choose the following Application Signatures and add them to the List:
- SOCIAL-NETWORKING Facebook – Poke Action 1 (6668)
- SOCIAL-NETWORKING Facebook – Poke Action 2 (6669)
- Click the OK button.
- Verify that your match object was created correctly by moving the cursor over the “info” button.
- Stage V - Create App Rule
Complete these steps in the GUI in order to create the App Rule. The App Rule is a policy that uses a Match Object and ties it to an Action Object.
- Navigate to Firewall > App Rules.
- Click on the Add New Policy button.
- In App Control Policy Settings, select the following:
- Policy Name: Block Facebook Poke Policy (type this in)
- Policy Type: App Control Content
- Address: Any
- Match Object: Block Facebook Poke
- Action Object: Reset/Drop
- Users/Group: Included: All
Note: App Control Policy Settings field selection definitions:
- Policy Name – This is the name that you provide for the policy
- Policy Type – the type of policy
- Address – IP Address or group of IP addresses that we are applying this policy to
- Match Object – what the firewall is looking for.
- Action Object – action that the firewall will take once it finds the match object
- Users/Group – user or group that this App Rule applies to
- Click the OK button
- Confirm that the policy is created correctly on the App Rules main page.
- How to Test
Complete these steps in order to test the Application Firewall configuration.
- Log into the network as a domain user.
- Open a friend’s profile and click on the Poke button.
- The connection will be dropped and nothing will happen. You will notice that your friend has not been poked.
- Log into the SonicWall firewall and navigate to Log > View. You will see the following Alert messages on the SonicWall firewall log.
- How to Troubleshoot
Check the following items in order to troubleshoot this configuration:
Symptom
|
Resolution
|
No Application Firewall Licensing
|
Purchase Application Firewall License from your Dell SonicWall rep.
|
Block Facebook poke Application Rule is in place and Application Rules is enabled globally, but Facebook poke is not being blocked.
|
Enable Application Control on the local network zone.
|
Block Facebook poke Application Rule is in place and Application Control is enabled locally on the LAN Zone, but Facebook poke is not being blocked.
|
Enable Application Rules globally
|
When opening a web browser, you keep getting Certificate errors.
|
This is due to how DPI-SSL works. Because it re-encrypts the traffic with its own certificate, and that certificate is not a publically accepted certificate, your web browser will not recognize it and then give you the certificate errors. You can prevent this by installing the SonicWall Firewall’s certificate in your web browser as a “Trusted” certificate. This will resolve this issue.
|
- Related Resources
SonicWall OS 5.8.1 Administrator’s Guide
Application Rules Overview http://help.mysonicwall.com/sw/eng/7630/ui2/70/Policies_AppControl_AppRules_Snwls.html
UTM: Using Application Firewall to Bandwidth Limit Bittorrent https://www.fuzeqna.com/sonicwallkb/consumer/kbdetail.asp?kbid=4426
UTM: Using SonicOS 5.8 and App Rules for Granular Control of Access to Facebook https://www.fuzeqna.com/sonicwallkb/ext/kbdetail.aspx?kbid=8934
For other Application Signatures that are on the SonicWall firewall, you can look up which Category group and Application group an Application Signature is in by using the search engine on the following page: https://software.sonicwall.com/applications/app/index.asp?ev=cat
UTM: Integrating LDAP/Active Directory with Sonicwall UTM Appliance https://www.fuzeqna.com/sonicwallkb/ext/kb7806-utm-integrating-ldapactive-directory-with-sonicwall-utm-appliance?mode=searchresults
Last Updated on 5/23/2013